1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
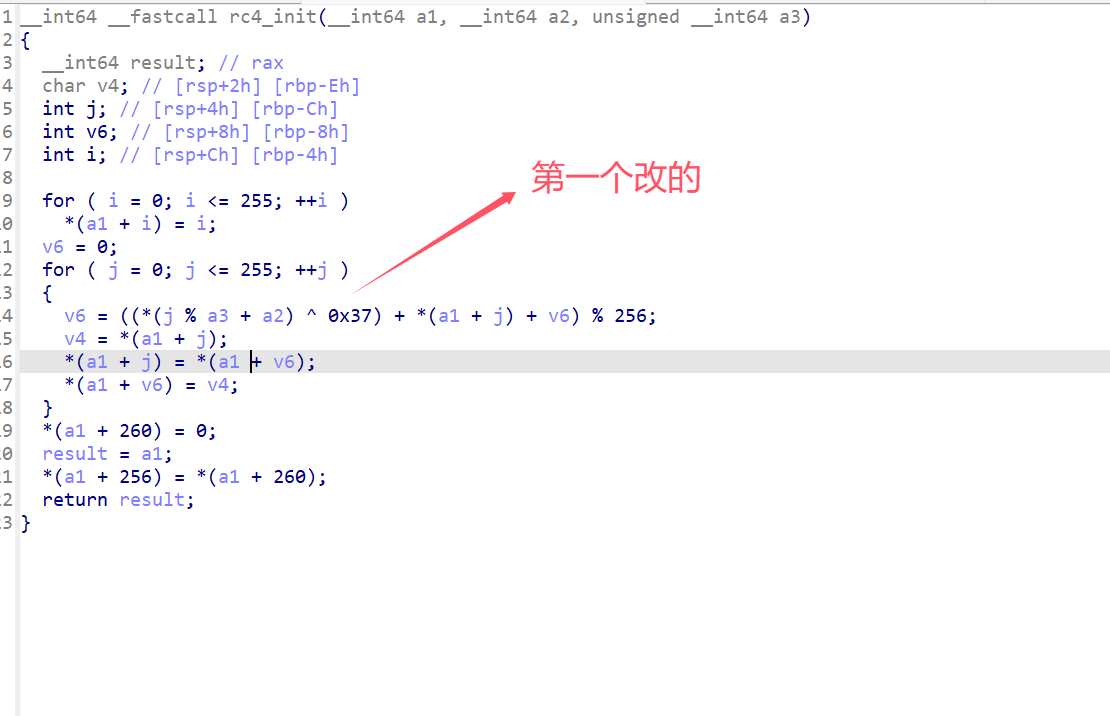
| def rc4_init(key):
# 初始化 S-box
S = list(range(256))
j = 0
key_len = len(key)
# KSA (Key Scheduling Algorithm)
for i in range(256):
modified_key_byte = key[i % key_len] ^ 0x37 # 密钥 XOR 0x37
j = (modified_key_byte + S[i] + j) % 256
S[i], S[j] = S[j], S[i] # 交换 S[i] 和 S[j]
return S, 0, 0 # 返回 S-box, i, j
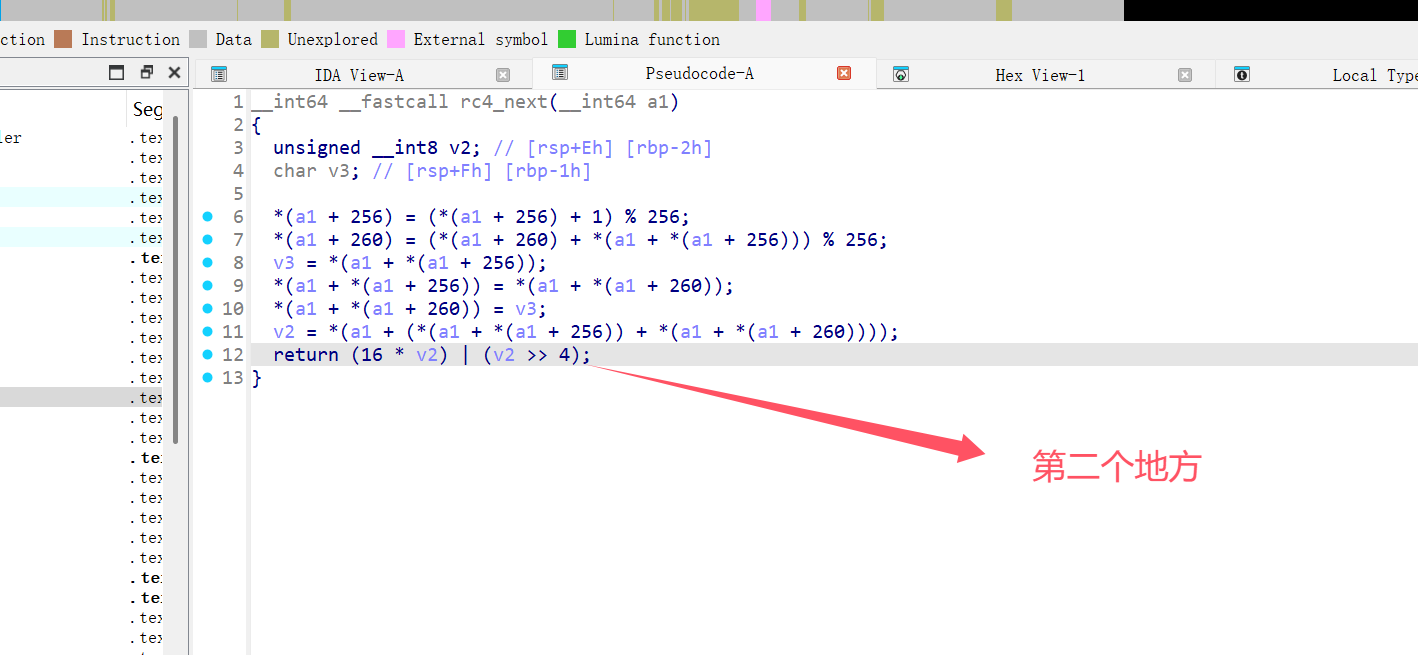
def rc4_next(S, i, j):
# PRGA (Pseudo-Random Generation Algorithm)
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i] # 交换 S[i] 和 S[j]
# 计算密钥流字节
keystream_byte = S[(S[i] + S[j]) % 256]
# 逆 nibble-swap (高 4 位和低 4 位交换)
swapped_byte = ((keystream_byte << 4) | (keystream_byte >> 4)) & 0xFF
return swapped_byte, i, j
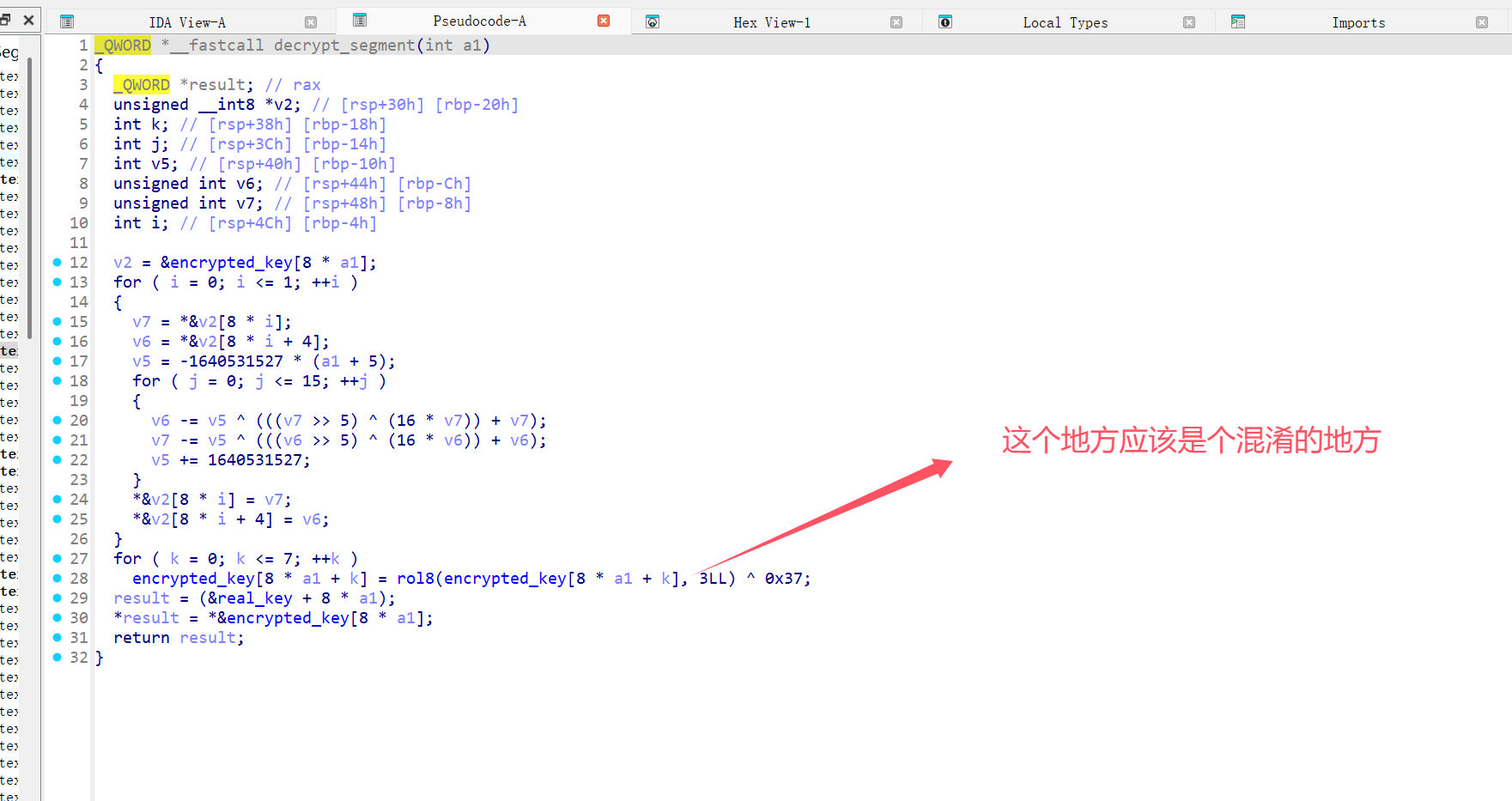
def rc4_decrypt(ciphertext, key):
S, i, j = rc4_init(key)
plaintext = []
for byte in ciphertext:
keystream_byte, i, j = rc4_next(S, i, j)
plaintext_byte = byte ^ keystream_byte # XOR 解密
plaintext.append(plaintext_byte)
return bytes(plaintext)
# 示例用法
key = b"EC3700DFCD4F364EC54B19C5E7E26DEF6A25087C4FCDF4F8507A40A9019E3B48BD70129D0141A5B8F089F280F4BE6CCD" # 替换成你的密钥
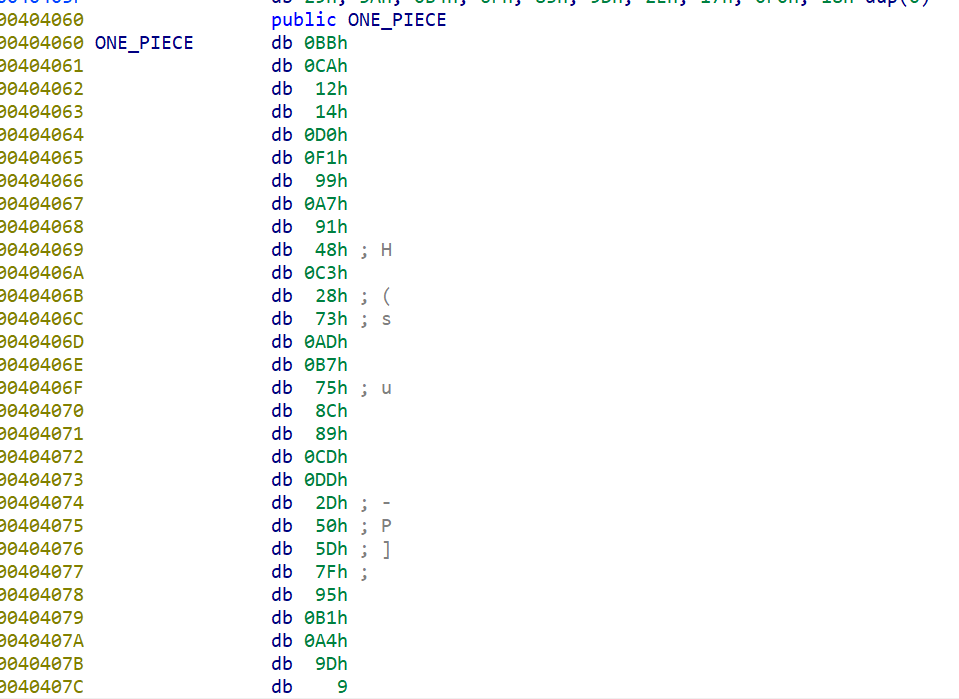
ciphertext = [ 0xBB, 0xCA, 0x12, 0x14, 0xD0, 0xF1, 0x99, 0xA7, 0x91, 0x48,
0xC3, 0x28, 0x73, 0xAD, 0xB7, 0x75, 0x8C, 0x89, 0xCD, 0xDD,
0x2D, 0x50, 0x5D, 0x7F, 0x95, 0xB1, 0xA4, 0x9D, 0x09, 0x43,
0xE1, 0xD2, 0xE9, 0x66, 0xEA, 0x18, 0x98, 0xC6, 0xCC, 0x02,
0x39, 0x18] # 替换成你的密文
plaintext = rc4_decrypt(ciphertext, key)
print("Decrypted:", plaintext)
|